Password Hygiene
Passwords are the bane of everyone's online existence these days. You hate them. I hate them. Everyone hates them.
But to state the obvious: Passwords are important and you need to do them correctly.
Back in the day, the 1990s, when the internet was just a wee tot, an eight character password was considered reasonably safe. And the risks of reusing passwords on multiple sites wasn't that big of a deal. Heck, there weren't that many sites. Not so today.
Spend a few minutes reading all about passwords, see what you really need to do in the 21st century, and what the future might look like.

Password complexity today
What we're all doing wrong today
Passwords, as a security method, are not inherently defective. Passwords can work and provide adequate protection to an online account. The problem is that most of us aren't following good password hygiene.
I'm not saying passwords are totally blameless. There's a lot to hate about passwords because it's too easy to do it wrong. But if we'd "do passwords correctly" then they'd do the job they're meant to do. I have well over 500 credentials that I need to keep track of and yet I manage just fine. Passwords, for me, aren't a pain at all.
The sad fact is that most people aren't managing passwords securely. Who can blame them? There's bad and conflicting advice on what to do and it's PITA besides.
Here's a list of bad practices that I've seen, in no particular order:
- Passwords that are too short
- Reusing the same password, or rotating between the same small number of passwords, on multiple sites
- Making new "unique" passwords by simply adding a digit or something
- Choosing passwords that are too easy to guess (e.g. names and birth dates)
- Choosing passwords based on famous people or quotes
- Choosing passwords that are easy to brute force
- Storing passwords in insecure ways such as the Notes or Contacts app on your phone
- Not having a password or PIN on your phone
- Not storing passwords in some manner (relying on memory only)
- Not using multi-factor authentication on sensitive sites that offer it, like your email or bank
- Writing down passwords on random scraps of paper (a dedicated book is ok)
- Using "Leet speak" -- that is, weird character substitutions.
Now lets discuss the above sins one at a time and how to repent.
1. Passwords today should be no less than 15 mixed characters, 20+ is best. "Mixed" means having something from all four character groups: 1) lower case, 2) upper case, 3) number, and 4) non-alphanumeric "special" characters.
Why? By including at least one character from each of the four groups, you are increasing "entropy". In short, more entropy means less predictability, less organization, more randomness. And longer length makes brute force attacks take longer.
2. Every web site that you have to sign-up to use, no matter how unimportant, deserves its own password.
Why? Because if you use the same password on multiple sites and one of those sites gets hacked and all the passwords are stolen, then it makes it far easier to log into your accounts on the other sites where you used that same password.
3. Making a new password by slightly modifying an existing password, maybe by adding a digit or character to the end, isn't good enough. You should create a substantially new password each time you need a new one.
Why? Password "crackers" (hackers who figure out passwords) already know these tricks. Part of their strategy is to make slight alterations to known passwords just like you might do. And they are pretty dang smart about it, too.
4. Using birth dates and family names are too easy to figure out.
Why? In the age of social media with its lack of privacy, and data breaches, it's not that hard to figure out these kinds of passwords.
5. Similarly, using the names of celebrities or notable quotes, isn't as safe.
Why? Password crackers have dictionaries of very nearly every password that has ever been stolen in a data breach. If someone else used the same famous person or quote as a password that you used, then finding that password becomes far easier. Best to use passwords that are only meaningful to you -- but again, not names or birth dates.
6. Short, non-complex passwords are easy to brute force.
Why? A "brute force" attack is trying every combination of characters. The longer and more complex your password, meaning you followed the advice in #1 above, then the harder it is to guess by trying all possibilities. For more info on what a brute force attack actually entails, see the next section titled "Password Crackers Are Smart"
7. Storing your passwords in the notes or contacts app on your phone is really insecure. If you are doing this then you really need stop!
Why? Notes and contacts aren't always encrypted. And depending on your email service, those notes and contacts may be synced to a cloud server where they can be accessed if someone sussed out your email password. Or if someone managed to get a hold of your phone while it was unlocked, even for just a minute, they could steal all those passwords.
8. If your phone doesn't have a password or PIN set up then you are really asking for it.
Why? Even if you don't store passwords on your phone, it's a good bet that you at least get email on your phone and, obviously, phone calls and text messages. If your phone is lost or stolen, and there's no PIN, then the finder could quite easily figure out your important accounts (by reading your email), perform password resets, then login to those sites, lock you out, then start wiping you out financially. Losing a phone with no PIN can lead to a catastrophic data breach that can ruin your year.
9. If you are practicing good password hygiene as recommended here then there's no possible way you'll remember them all. You should write them down (Yes, that's safe. Just keep your password notebook securely hidden). You can buy "password notebooks" that contain templates for filling in all the important info. You can also use a password manager. More on that below.
10. Multi-Factor (or Two-Factor) Authentication (MFA/2FA) is when you must provide both your password and a code that's usually texted to your phone. This is recommended for super sensitive sites like your email, bank, or sites where you can buy things like Amazon.com.
Why? MFA/2FA helps protect your account in the event your password is compromised. The attacker might know your password, but without your phone, they cannot get the code number required to complete the login.
n.b. MFA/2FA isn't bulletproof. There are hacks where people are socially engineered (tricked) into providing the code number. That's additional work for the attacker and definitely complicates things, so MFA/2FA is still recommended.
11. Writing down passwords in a dedicated book is fine but not on random scraps of paper. Reread #9 above for best practices.
Why? You'll never keep track of 137 random scraps of paper, they'll get lost, believe me.
12. Using Leet Speak: Character substitutions that look similar. Examples include using zero as the letter O, using 1 as the letter I, using 3 as a backward E, using @ as the letter A, and so on. There's quite a few of them.
Why? As I'll discuss below, crooks are not manually trying passwords. It's all done automatically. Password cracking algorithms all know how to use leet speak so there's no security conferred there. Worse, it makes passwords more difficult to type in and mistakes are more common, risking an account lockout. It was never a good idea and and it still isn't. Don't use leet speak.
Click Here for a funny but very geeky cartoon that explains it.
Other tips to help prevent your password from being compromised:
- Avoid logging into sensitive accounts from any computer that isn't under your full time control. Never use computers in a hotel's guest business center to sign-in to an account; there's a chance it's been infected by a previous guest. Simple web surfing is fine, just don't sign-in to anything. Logging in using a friend's computer is safer but do so sparingly. When logging in on a computer that's not yours, use the browser's private mode. On Chrome, that's "incognito".
- Connecting to an open and unlocked public wi-fi should be done sparingly. It's far safer today than it used to be but it's still an attack vector. Better yet, if you can, connect your laptop to the internet using your smartphone's personal hotspot feature. Most phones and data plans allow that now.
Password Crackers are Smart
When a password cracker is trying to figure out passwords, they never start with the "brute force" approach. Brute-force simply means trying every possible combination of characters until a hit is made. Yes, it's one approach they use, but it's slow compared to other approaches so they save it for last.
Instead, they try popular password lists, common word lists, and apply programming rules in order to crack passwords without trying every possible combination. By combining these advanced techniques and using a powerful purpose-built computer, a password cracker can make billions of guesses per second. And that guess rate increases every year as newer and faster rigs are built. The rig pictured here costs less than $10,000, making it affordable to any determined hacker.
You might say "But how can a hacker make several billion guesses per second? No one can type that fast, and besides, won't the website they're trying to break into limit the hacker to 3-5 guesses?"?
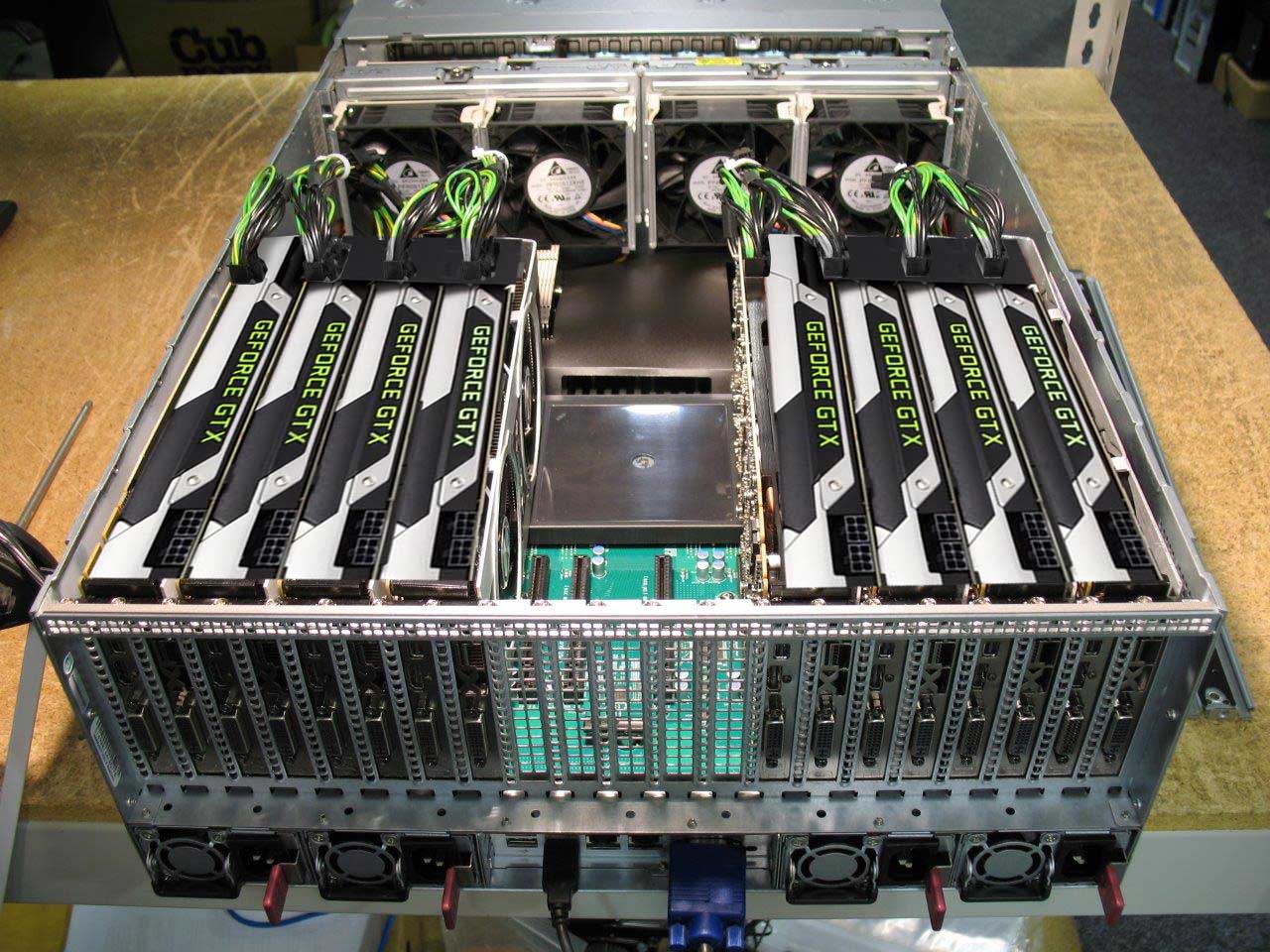
Custom password-cracking rig
That's not how password cracking works. Password cracking is performed offline against a stolen database containing millions of usernames and passwords. Such offline attacks aren't affected by web server frontend security that may limit you to just a few login attempts.
It's beyond the scope of this article to go into the highly technical details of how, exactly, password crackers do their thing. You can Google it for yourself -- be warned, that's a deep rabbit hole.
So you'll want to create passwords that are hard for a password cracker to guess, even though they are making many billions of guesses a second. How to do that?
Passphrases
Passphrases are an easy way to beef-up your passwords. It's better than using single-word passwords even with a number or two stuck to the end. One possibility is to think up 2, 3, or maybe 4 words that roughly describes the site that wants a new password. e.g. For your bank, it might be something like "MyDoughIsHere" or "HoldsMyMoney". Your Home Depot password might be "FixingOurHome" or "LotsOfLumber". You get the idea. Or those words can be completely random and silly.
To make it stronger, to satisfy #1 discussed above, you can add some numbers to it and a special character. In this case, the numbers could be the same for all your passwords because the "words" part of your password will be pretty long and unique if you follow my passphrase advice. So you could add a period, hashtag, comma, or other special character followed by any 3-4 digit number that's important to you in some way. Like maybe your street address as a child or your phone PIN.
e.g. "MyDoughIsHere+456" or "456+MyDoughIsHere" or something similar. The "+" and "456" could be on all your passwords and in the same spot so that's easy to make up new passwords for each site by just changing the words. Come up with your own pattern. Whatever custom method you choose, the resulting passwords should be at least 15 characters long and 20 is even better. You won't have to type these in more than once (usually) if you're using a password manager so having long passwords isn't a big deal.
The password advice I suggest above is for all practical purposes no less secure than a password made of totally random characters but it's a whole lot easier to type in correctly should you need to do that.
Halfway Exposed
Most online website accounts today want to use your email address as the "userid" portion of the "userid/password" credential pair. That's bad because it needlessly exposes HALF of what it takes to gain access to that account.
Back in the early days of the internet, most sites allowed you to create an arbitrary userid, so long as someone else hadn't already claimed it. Modern websites today have (mostly) moved away from that for the convenience of their users. Since a userid must be unique to the site, people had trouble coming up with one that wasn't already in use. Email fixes this because they are already unique. Problem is, for a credential pair, they're also very public.
Multiple Identities
Using separate email addresses, just like using a unique password, can help protect you if a website password database is breached. I know, I know... Unique passwords are already a pain. But unique email addresses, too!? Seriously??
Yes. But here's an elegant answer to that...
Gmail has a little-known yet incredibly useful "email alias" feature that lets you create special-use email addresses for all your (important) website accounts. By using a unique Gmail alias for each of your sensitive accounts, then if a different website is breached (email addresses and passwords stolen), the bad guys will never know what the email aliases are.
e.g. For your bank account, consider this sample Gmail account: johndoe+chase@gmail.com The portion in red, +chase, is the alias. You can make the alias whatever you want. +BofA, +Chase, +Kitties, or whatever pleases you. (The + must be present) Email sent to that address resolves to the root address johndoe@gmail.com and will land in the same inbox. If you use that alias for your bank login only, then no other web site will know that. So if some other website that you have an account on gets hacked, the bad guys won't know your bank alias, even if they know your root email address.
The alias feature is already available and working for all @gmail.com accounts.
Here's how to use it:
- Log into whatever sensitive account you want to protect with an alias, like your bank.
- Think up an alias such as +chase or a random word. Your email address for this bank account, becomes johndoe+chase@gmail.com
- Go to your profile settings for your bank and change your login email address. It's probably in the same place where you'd change your password, phone number, etc.
- You'll probably have to confirm the new email address. That confirmation will be sent to johndoe+chase@gmail.com. Since +chase is just an alias, then it'll automatically land in your regular johndoe@gmail.com email inbox.
- Make a record noting this in your password book or password manager.
You should repeat this for all your important and sensitive accounts, giving each one its own alias. For less important accounts, you could use your root email only. Or use a catchall alias for those, like +misc. Note that some websites won't let you use a + sign in your email address so that trick won't work for them. But most will allow it. I make extensive use of this feature.
Another cool use for aliases is that you can filter incoming email for special processing that is sent to that alias. e.g. Bypass the inbox, or mark it bright red to get your attention.
Just another of the many reasons to use Gmail.
Password Management
Even though passphrases can be easier to remember and, more importantly, easier to type in than a deliberately mangled single-word password, you'll still need to keep track of them if you want follow good password hygiene. There's several approaches you can take here.
A good old school approach is to buy a smallish 5x7 spiral notepad and dedicate an inch or so of space to each web account. That way, you have plenty of room for notes and corrections associated with each website. Use a pencil so you can edit later. Jot down everything you'd ever need to know: Username, password, answers to security questions, account numbers, etc.
That spiral notebook cannot be hacked from afar so it's actually a very safe way to record passwords. Write neatly so you can read it later and store the book in a safe place where kids and visitors or a potential thief aren't likely to find it. You can also buy notepads specifically for password storage that has spaces for all the important info. Look on Amazon.
Save all your passwords in a password-protected file (use a passphrase here, too). Then every time you edit and save the file, print out a copy as well so you'll have a hard copy, in case your computer dies. Microsoft Word or Google Docs could be useful.
The best solution is to use password manager. These are programs that securely store passwords and other sensitive info, synchronizes it all between your various devices, and auto-fills password boxes in your web browser. If your computer has a login password then this is safe.
More on Password Managers
Password Managers are programs that, well, manage passwords. But they do it safely and offer additional features. They hold all your passwords in a secure database. Password managers can also auto-fill password boxes in your browser and help you generate super-strong passwords for new online accounts that you create. I personally don't use the password-generate feature because I want to create passphrases, as I described above. But it's there if you want.
All the popular browsers (Chrome, Firefox, Edge, Safari, etc.) have password managers built-in. They work well but aren't compatible with each other. If you use multiple browsers like I do then you'll have to separately teach each one. 3rd party password managers fix that. They are cross platform (Windows and Mac) and work with most browsers to auto-fill your passwords.
Password managers also help protect you from phishing emails that try to trick you into logging into fraudulent, look-alike websites. While you, a silly human, may be fooled by a well-crafted fake Bank of America login page, a password manager would never be tricked like that. Using a password manager, you'll know right away if a login page is fake because the password manager won't auto-fill the username and password.
Another advantage to a 3rd party password manager is allowing you to store other kinds of sensitive non-password data, something that the built-in browser-based password managers don't do very well -- or at all. That might be tax info, combinations to padlocks, SSNs, security questions and answers, MFA/2FA backup keys, and other sensitive non-password info.
Such 3rd password managers include mSecure, 1Password, RoboForm, Bitwarden, and Dashlane to name a few. I would not recommend LastPass due to insecure practices by that company.
Most 3rd party password managers are subscription based but they aren't expensive.
Multi Factor Authentication
Multi Factor Authentication (MFA) or Two-Factor Authentication (2FA) is a feature increasingly offered by websites these days. When a website account is protected with MFA, then you must provide multiple (two usually) forms of identity in order to access the account. The first is your password as usual, and the second is generally a random six digit number displayed on your smartphone. This way, if a hacker managed to figure out your password, they would be unable to access your account because they would not have your smartphone and so could not get the six digit number. There are crafty ways around this, but unless you are being specifically targeted, the attackers will generally just move on.
If you have important accounts on a site that does not offer MFA the complain to them! Anything involving your money or confidential data should offer MFA.
Setting up 2FA is not entirely painless. It must be done correctly lest you lose access to your own accounts. e.g. Authorizing your phone to be the security token (shows the code number), creating emergency backup code keys, setting up alternate email address for account recovery, etc. This is where an I.T. pro like me comes in. I know how to set these up properly to keep you safe!
Insecurity Questions
Some websites ask you to give answers to one or more security questions as part of a new account signup process. Questions like "name of your first pet", "name of high school that you graduated from", "best childhood friend", etc... These questions are there to help you recover account access in case you forget your password. But it could be insecure if you give truthful answers. Bad guys can figure all this out easily enough using social media, stolen data dumps, and social engineering techniques.
Instead, provide false nonsense answers to these questions. One of my clients answers them all with different brands of beer. Just remember to jot down your false answers and the question that it goes with so you can enter the answers correctly later on if the need arises. But since you'll be following my advice by recording your passwords in a notebook or using a password manager, then you won't ever forget your passwords in the first place. Right?
Death of Passwords?
Most big tech firms (Apple, Google, Amazon, Microsoft, Meta, to name a few) are developing and encouraging the use of Passkeys, an authentication system that relies on proving thyself worthy by using non-password methods. That can include biometric features such as facial and fingerprint recognition, it can include physical devices such as a Yubikey (a small USB thumb drive-sized device), and your phone.
These passwordless methods are far less susceptible to compromise due, in part, to not being based simply on "something you know" (a password). Fraudulent login screens would no longer work because there's no password to type in.
Setting these up correctly is important! Since Passkeys rely more on physical devices then it's critical that you have recovery methods in case you don't have access to any of those devices.
Passkeys is a fundamental change in how online account authentication works, Because of that, it's not catching on quickly. It'll likely be years before Passkeys become common.
Eggs in One Basket
In most large companies, computer and network resources are accessed through a thing called Single Sign On (SSO). This way, an employee only has one set of credentials that opens up everything they are allowed access to.
There's a similar thing in the non-corporate, public "retail space" called an Identity Provider, or "IDP". You've probably seen this even if that term is unfamiliar. When you create a new account on some online services, you may be offered to "Sign in Using Google" (or Facebook, etc.) instead of making a fresh account for that site. In this example, Google is the SSO IDP through which you can gain access to this new site. Sounds handy, right? Don't have to think up a new password. Woot!
Let's briefly look at the pros and cons of using Google, or any IDP, as your authentication method.
Pros:
- No new password to think up, remember, write down, or type in later
- Somewhat less likely to be compromised
- Certainly, a smoother authentication process
Cons:
- If Google's IDP architecture were compromised, all your sites that are authenticated by Google could possibly also be compromised.
- Single point of failure. If Google's IDP is unavailable or malfunctioning, you could possibly have difficulty accessing sites that rely on it
- Involving Google to yet one more thing about you. I'm not especially keen to do that.
Man Without a Country
As bad as we are at using passwords to protect our accounts, and as much as security professionals would love for them to go away, most passwordless methods rely on some sort of device to authenticate. What if you had no access to any of your devices? e.g. You're traveling and suffered the loss of your luggage, devices, and everything except maybe your wallet and passport. Or your home burns down and you manage to get out with little more than the shirt on your back.
OK, so you'd buy a new phone and maybe a laptop. But how would you bootstrap your way into your online accounts from a virgin device? How would you prove your identity when all your identity-proving devices were lost, stolen, or damaged? You'd be a man without a country so to speak.
Here's where an old-school password, possibly along with a never-changing, never-expiring (until it's used) security code would come in handy. That all-important password is one you must never reuse and never forget because it unlocks everything else. The security code is just another optional layer. You would probably have the codes printed on a slip of paper in your wallet.
When I travel, I have my one-time security codes printed on several slips of paper and scattered about my various articles: wallet, carry on, checked bag, and my wife and her articles. Those codes are not identified in any way so if I lost one and someone found it, they'd be useless.
Brave New World
Security professionals everywhere constantly grapple with these opposing forces: Security vs. Convenience. TSA, metal detectors in government buildings, in sports venues, concerts, and more. Same thing applies to computers and websites. Greater security usually means more hassles for legitimate users.
Imagine the ruin you could face if your bank or brokerage accounts are hacked into. If your business email or cloud accounts like Dropbox were hacked and your confidential info or your client's was ransacked and exposed, it would for a pretty bad day.
I know that all the things I've discussed and suggested above can be unnerving and even a pain to follow. But this is the reality of living online today. Security is simply too important to neglect and as our lives and businesses are ever more conducted online, good security is critical. Disregard at your peril.